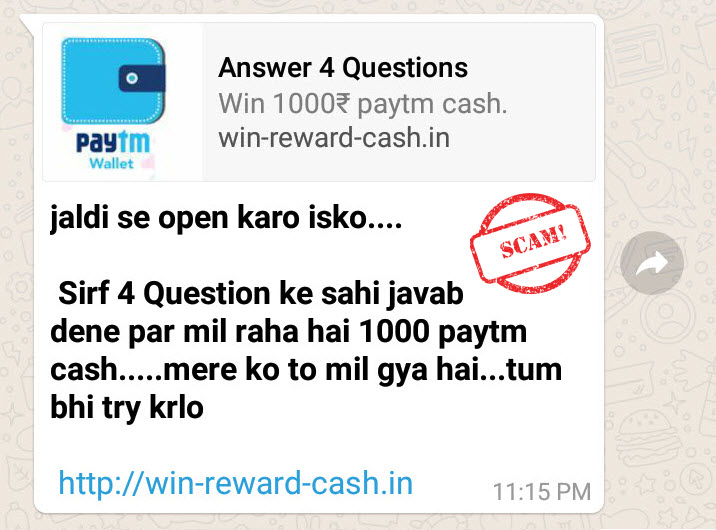
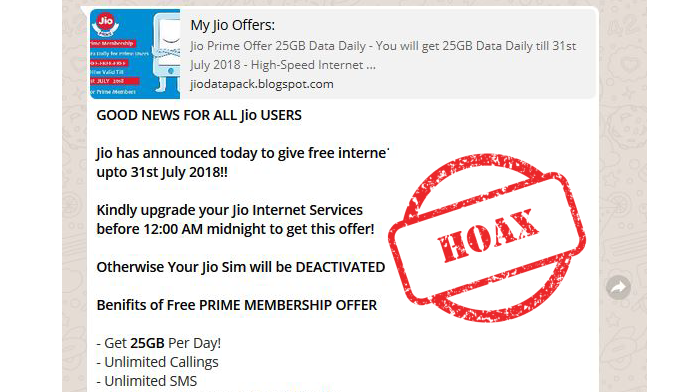
9 security tips for using mobile payment apps
Do you find it convenient to shop and bank online using mobile payment apps? Most would have ‘yes’ as an answer. But, are we letting ‘convenience’ overshadow ‘security’? An attacker can easily get hold of your personal and banking information if the app or the mobile site you are using is compromised. The chances of this […]