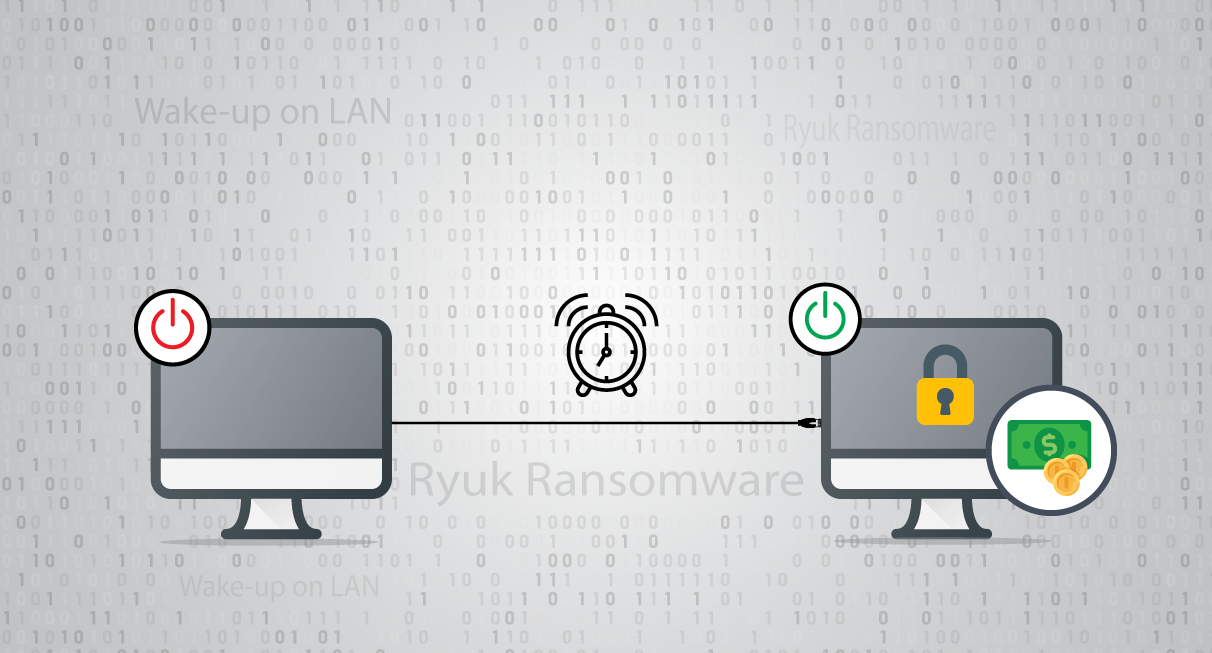
A Deep Dive Into Wakeup On Lan (WoL) Implementation of Ryuk
Quick Heal Security Labs recently came across a variant of Ryuk Ransomware which contains an additional feature of identifying and encrypting systems in a Local Area Network (LAN). This sample targets the systems which are present in sleep as well as the online state in the LAN. This sample is packed with a custom packer. The final […]