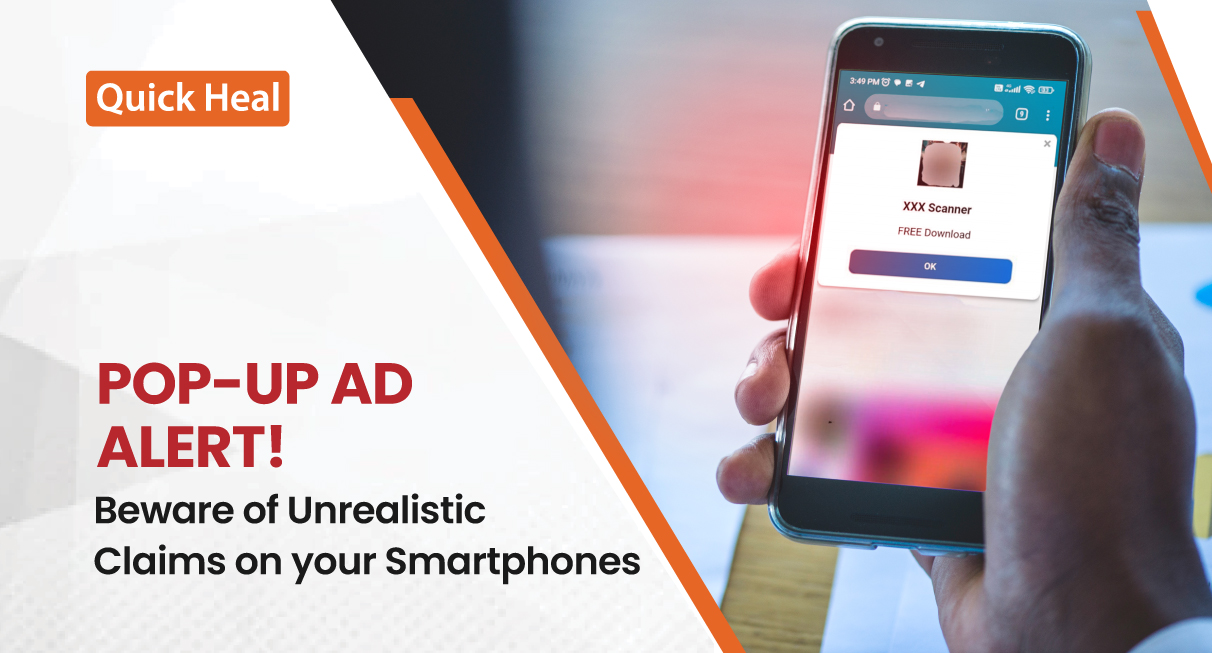
Can You Outsmart Cybercriminals? Stay One Step Ahead with a Powerful Antivirus Solution!
Let’s face it: the digital landscape is a treacherous realm. Cyber attackers keep hunting for vulnerabilities, finding ways to breach your digital defenses. You must have heard about Aadhar/PAN card fraud, data leaks, money stolen from accounts, and whatnot. You might have even heard your parents complaining about Facebook fraud and fake calls. But you […]