India – the 4th Most Targeted Nation by Phishers!
In an earlier post, we had discussed how cyber attacks against India is increasing rampantly. In this post, we give you a brief about how phishing attacks are affecting Indian enterprises and what can be done to contain the problem.
In Q3 of 2013 (July – September), about 1,25,212 phishing attacks occurred globally. Out of that, 3% was directed against India. This amounted to a loss of a whopping Rs 328 crore ($53 million). Apparently, the country ranks 4th in the hit list of phishers; according to a report presented by RSA.
The US still ranks the first, followed by Germany and the UK. The losses incurred by businesses in these countries are as follows:
US – loss of $882 million
Germany – loss of $294 million
UK – loss of $133 million
A little Background into Phishing
If there is anything in the IT security world that can aptly related to the phrase ‘Old is Gold’, it is phishing. It is one of the oldest tricks in the book of hackers. A typical example of a phishing scam is something like this:
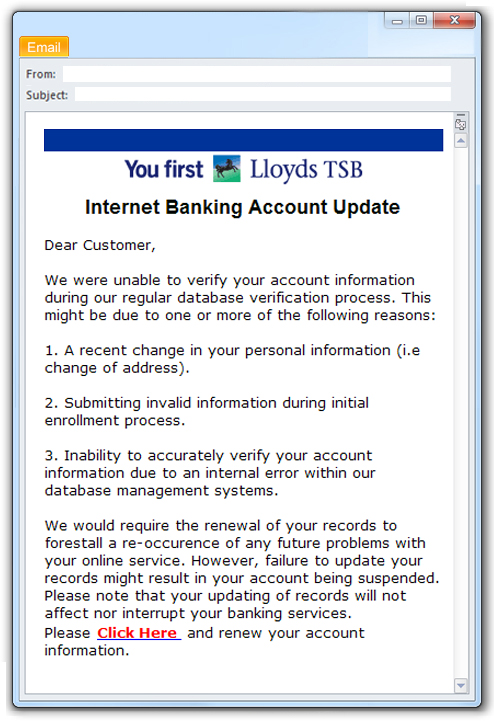
Ted receives an email message from his bank. The email looks genuine with all the look and feel of the bank, its logo, etc. The email informs Ted that his bank is in the process of updating his records, to enhance his account’s security. For that, Ted needs to renew and update his bank account information. The email also has a link to a web site where Ted has to update his records. Ted clicks the link, visits the web site (which looks like the real one), and he gives away his bank account details. The next thing Ted might realize is, his account is automatically being drained. What happened there? Well, Ted just got phished!
Here is a sample of a phishing email that looks like it has come from Lloyds Bank:
You can read more about phishing scams and how you can avoid them in this post.
What Can Enterprises do to tackle the Phishing Problem?
Given the rampant increase in phishing attacks, enterprises must focus on two key aspects:
A. Making employees aware about the best practices to avoid being scammed by phishers. Some of them are listed as follows:
a). Deleting emails coming from unsolicited and unwanted sources.
b). Avoiding giving away bank information or other confidential information over emails, calls, and SMSs.
c). Avoiding clicking links in email messages. Accessing a site by typing its URL in the web browser is safer.
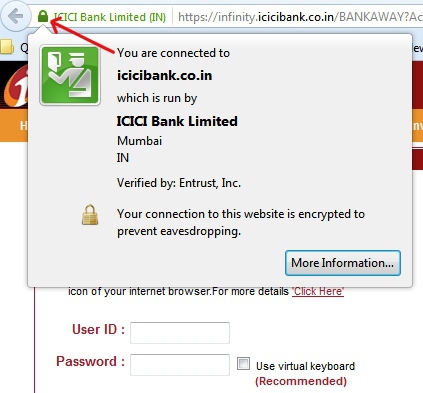
d). Verifying a web site’s identity and security status before giving away financial information. A secure web site has a lock icon and its URL begins with ‘https’.
B. Deploying a Unified Threat Management (UTM) and End Point Security system to block fake, fraud, phishing, and infected web sites.
a). The web security feature of Quick Heal’s End Point Security, has been designed to scan web pages visited by users. If the web site shows any fraudulent or phishing activity, it is blocked.
b). Another feature of Quick Heal EPS is Web Filtering. With its help, the types of web sites that are suspected of launching phishing attacks, can be blocked.
c). Quick Heal’s UTM is another security solution that provides an extra layer of security to enterprise network. Among other features, its content filtering feature blocks Web sites that show suspicious or unsafe behavior.
Phishing may be a difficult nut to crack, but in most cases, it requires user intervention. As long as the user is careful about sharing confidential or financial information online, they can keep phishing scams at bay.