Watering Hole Attack – An Overview
Guess what would be a better way for a predator to stalk its prey, rather than chasing it? Well, waiting patiently at a watering hole, where its prey would eventually turn up. Strangely, in the online world, hackers are also using the same strategy to trap their victims. This blog gives you an overview of watering hole attack.
What is a Watering Hole Attack?
We are discussing here a new breed of online fraud called “watering hole attack” – an evolved form of spear-phishing. In spear-phishing, the scammer intends to target individual victims by sending malware-infested emails, and luring them into giving confidential information. A watering hole attack, on the other hand, does not use any such emails, for it infects an entire website the victims of a targeted business or organization are most likely to visit.
In other words
A watering hole attack is like poisoning an entire grocery store of the town and waiting for someone to buy from it, instead of luring each victim into buying a poisoned item.
The Working of the Attack
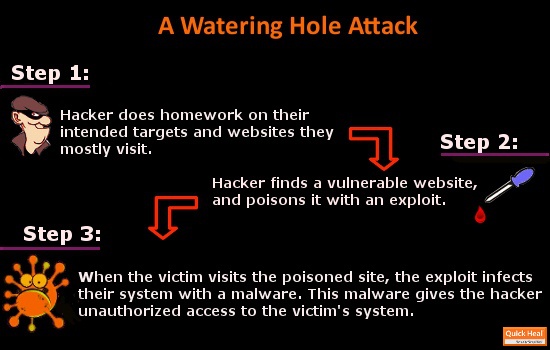
Step 1: The scammer does homework on its targeted victims and “trusted” websites they frequently visit or are most likely to visit. For instance, mobile developers usually visit a developer forum, and so on.
Step 2: Once these websites are identified by the scammer, they are tested for security vulnerabilities. If any such vulnerability is found, then the scammer injects the website with an exploit [a piece of data or a series of commands].
The Final Blow: When the victim visits the compromised website (the “watering hole”), their system is scanned for software vulnerabilities (old and/or new) corresponding to the injected exploit. And if the system is found so, then the exploit drops malware onto it, allowing the attacker to initiate malicious activities. In most cases, the malware might be a remote access Trojan, that can invite other malware to enter the system.
Why Watering Hole Attack is Effective?
Experts say, watering hole attack is an ingenious form of fraud, for it targets websites that are legitimate, frequently visited, and less likely to be blacklisted. If you regularly follow your local weather forecast website, then you might have fewer reasons to suspect it as a malicious website. Same goes with mobile developers, who frequent a variety of websites (developer websites, forums, etc.) to collate essential information or to discuss their projects. Given such a scenario, even training employees to be on guard for such web attacks is futile, according to most security officials.
The Zero-Day Advantage
Watering hole attacks are also effective, for they have the “zero-day exploits” card in their deck. These exploits take advantage of security holes or vulnerabilities that have surfaced recently and are yet to have any solutions or fixes. So, once these zero-day threats strike, the targeted victim is left with less or no defence at all.
Common Targets of Watering Hole Attacks
• Defence sectors
• Academic sectors
• Government organisations
• Financial services
• Healthcare industry
• Utilities sectors
Companies that were Recently Attacked
• Facebook
• Apple
• Twitter [the attack compromised account credentials of 250,000 users on Twitter]
• Microsoft
• U.S. Department of Labor
• Council on Foreign Relations (CFR)
• WTOP.com
• Federalnewsradio.com
• Dvorak.org
The web security feature of Quick Heal Security Solutions employs real time cloud-based protection and browser sand box. The cloud-based protection blocks malware-infected websites (“watering holes”), and the sandbox shields the user’s system against zero-day attacks. As everyday Internet users, implementing all such security features is the best we can do to evade scams such as watering hole attacks.