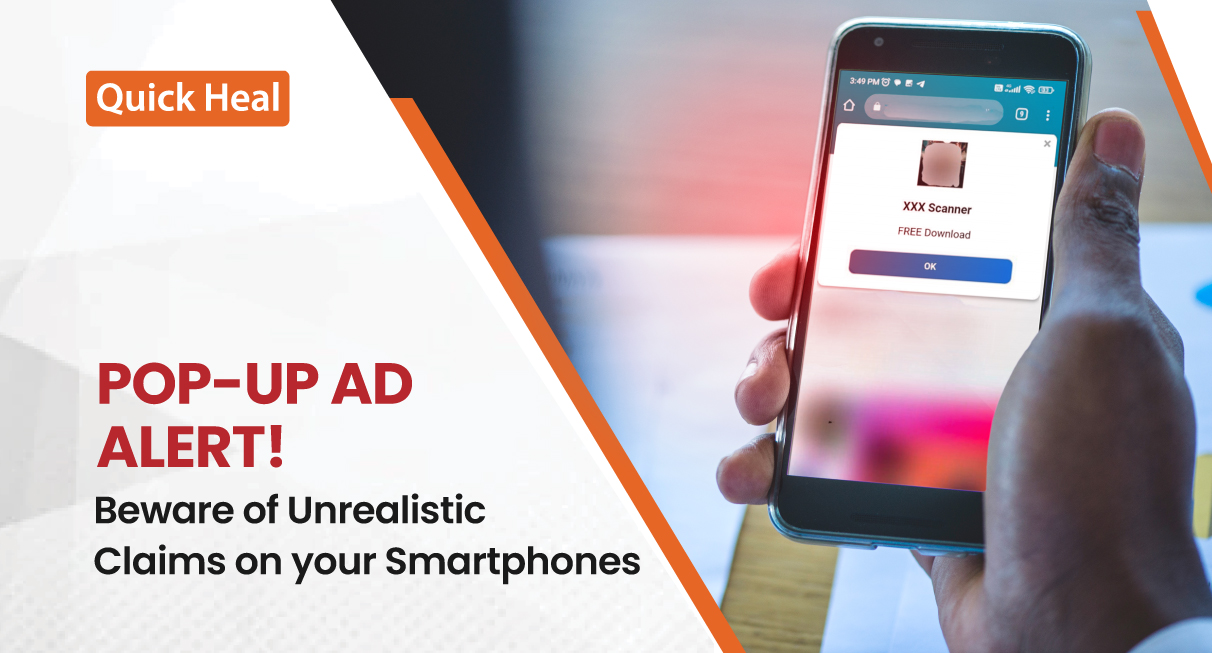
Worried About Your Phone Getting Hacked? Secure Your Device With The Best Antivirus!
Ever felt like there’s a tiny, invisible threat lurking in your pocket? Well, guess what? You might be pretty close. In today’s tech-savvy world, everyone’s lives practically revolve around their smartphones. From shopping to banking, booking travel to trading stocks, phones got you covered. Imagine if someone was peeking into everything you do on your […]